The six steps of the pdlc are analyse the problem design the program code the program test and debug the program formalize the solution and maintain the program.
Steps of the information security program life cycle dod.
It covers the information security program lifecycle which includes who what how when and.
During this course you will learn about the dod information security program.
Dod information security program.
What are the steps of the information security program life cycle.
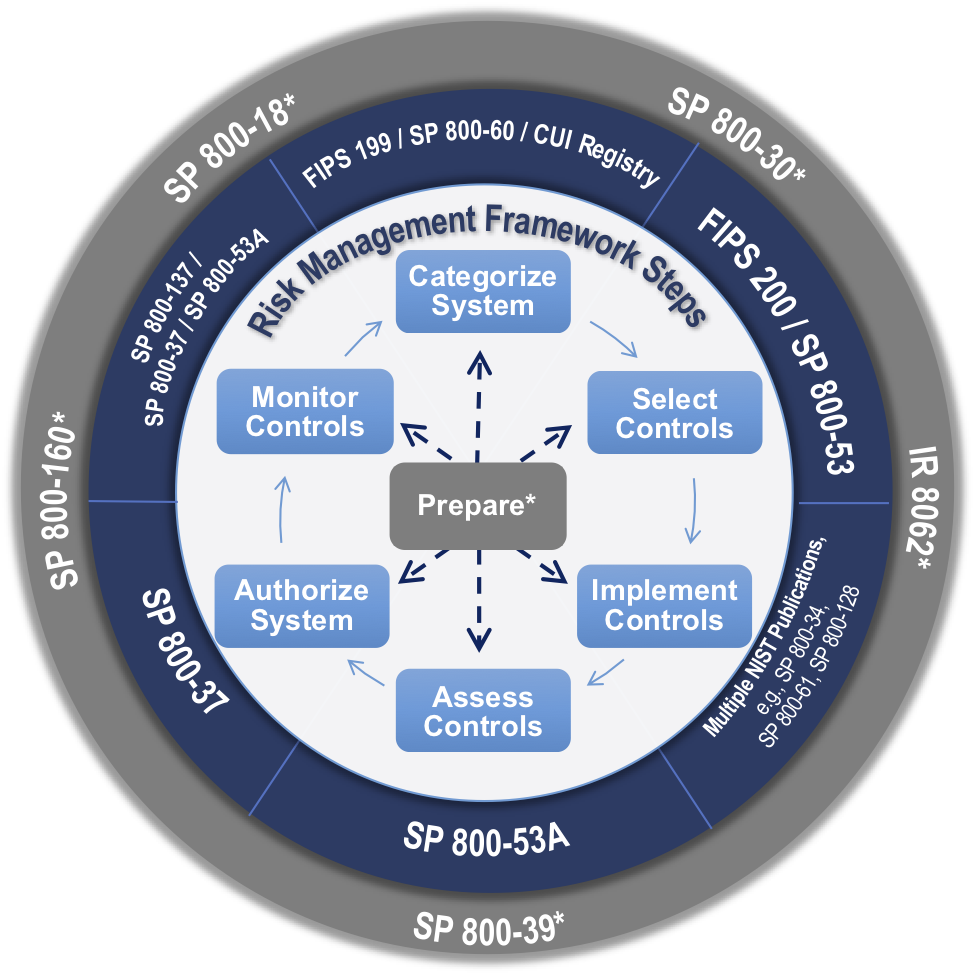
The selection and specification of security controls for a system is accomplished as part of an organization wide information security program that involves the management of organizational risk that is the risk to the organization or to individuals associated with the operation of a system.
This course will provide a basic understanding of the program the legal and regulatory basis for the program and how the program is implemented throughout the dod.
A information security program is the set of controls that an organization must govern.
Control selection implementation and assessment.
It is important to understand that a security program has a continuous life cycle that should be constantly.
Life cycle management lcm life cycle management is the implementation management and oversight by the designated program manager pm of all activities associated with the acquisition development production fielding sustainment and disposal of a dod system across its life cycle jcids operation manual.
This publication describes the risk management framework rmf and provides guidelines for applying the rmf to information systems and organizations.
Classification safeguarding dissemination declassification and destruction the unauthorized disclosure of confidential information could reasonably be expected to cause to our national security.
The management of organizational risk is a key element in the organization s information security.
Assigning a lower classification level to classified information because the information requires less protection in the interest of national security.
The rmf provides a disciplined structured and flexible process for managing security and privacy risk that includes information security categorization.
2 provides guidance for classification and declassification of dod information that requires protection in the interest of the national security.