In order to obtain a security guard license in new york state unarmed you must complete the following steps.
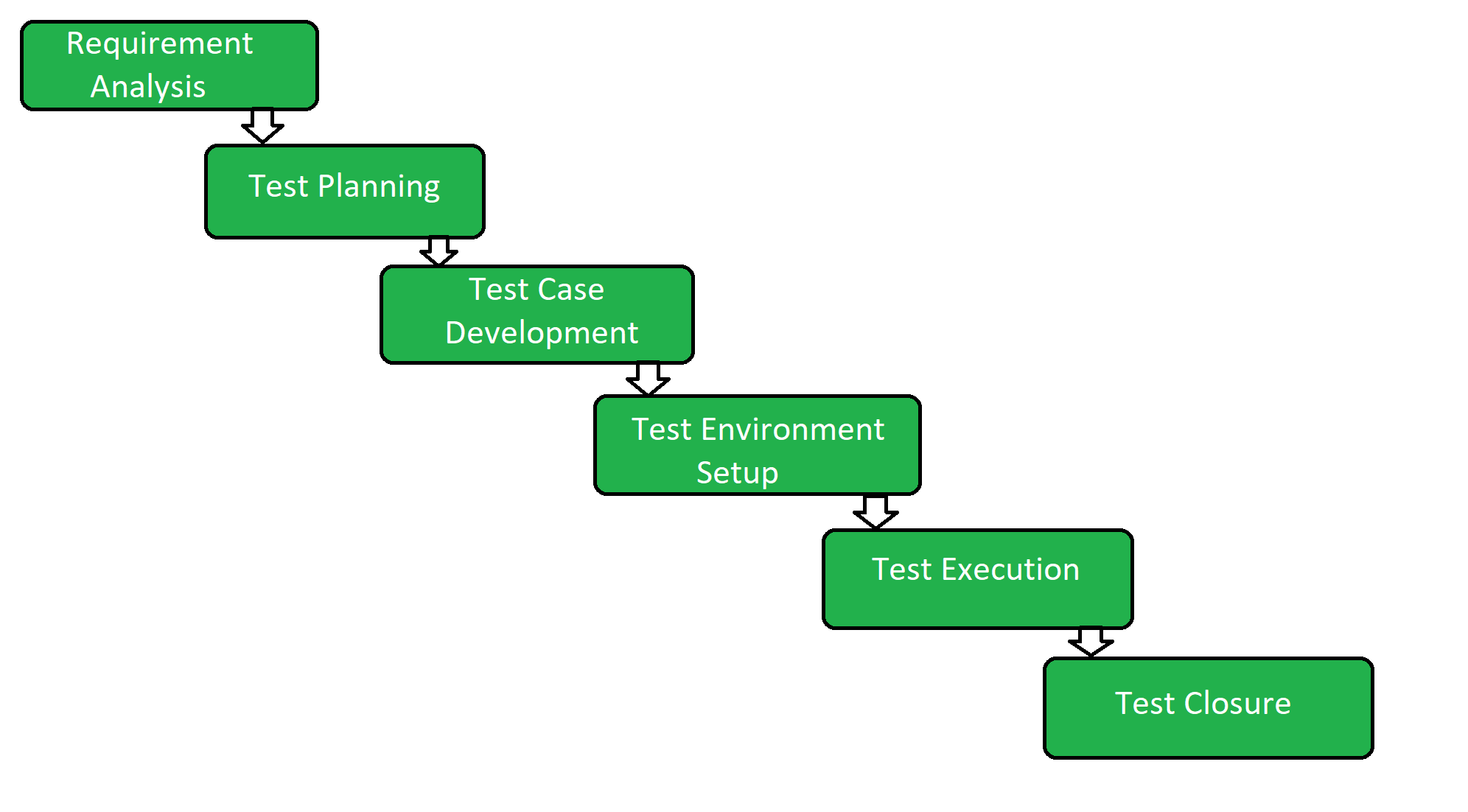
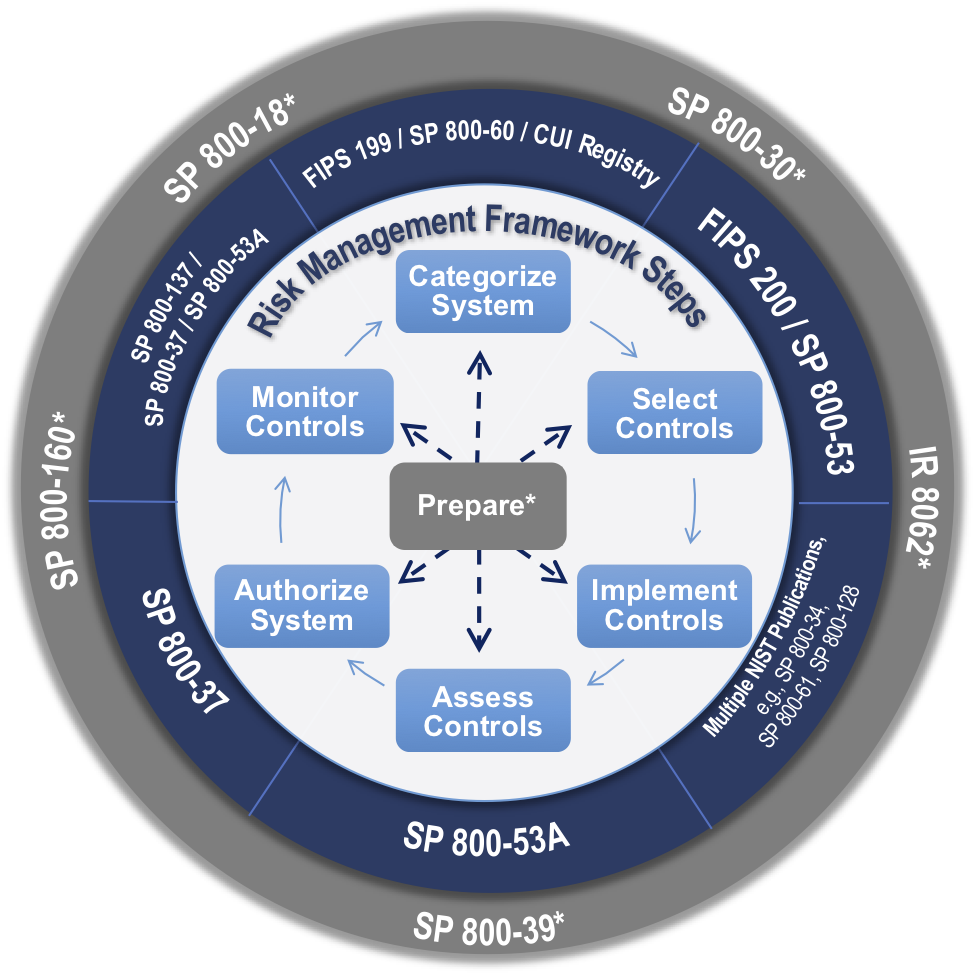
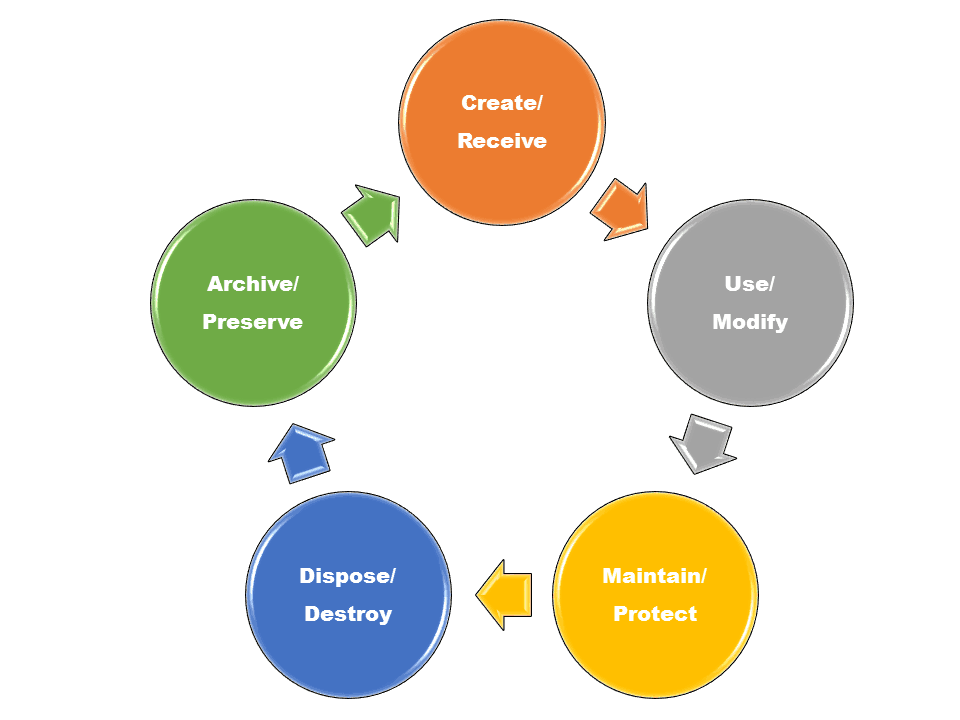
Steps in the information security program life cycle classification.
It covers the information security program lifecycle which includes who what how when and why information such as a document like me is classified known as classification protected known as safeguarding shared known as dissemination downgraded declassified and.
Classification safeguarding dissemination declassification and destruction.
Added 44 days ago 8 18 2020 11 26 51 pm.
Classification safeguarding dissemination declassification and destruction.
Are the steps of the information security program lifecycle.
Classification management involves the identification marking safeguarding declassification and destruction of classified national security information generated in government and industry.
A information security program is the set of controls that an organization must govern.
It encompasses the life cycle management of classified information from original classification to declassification.
What are the steps of the information security program life cycle.
The three levels of classification are top secret secret and.